GrpcConnectionPoints Configuration
The GrpcConnectionPoints JSON block is used in each process settings file to define how to connect to other processes and which certificates to use.
GrpcConnectionPoints
The GrpcConnectionPoints code block in the Jubilant process configuration file details how that process communicates with other Jubilant processes. This includes what server or client certificates to use, along with the host name / ip address and port on which to serve its own service, or to how connect to a remote service.
DefaultCertificates
This is the configuration block where the certificate thumbnails required by this process are specified. Information about the Configuration IDs are shown in detail and in tabular form in this document.
An example DefaultCertificates block could look like:
{
"DefaultCertificates": {
"ClientCertificateThumbprint": "90483663534F11B136F923FF314DF66A8B35FC7A",
"ClientManagementCertificateThumbprint": "5F3C40E3A619F5D8284B61C9A0D6B7471B0E9D1E",
"ServerCertificateThumbprint": "B6F1912725748D8ADFA1DBC1E421C7650477750D",
"ClientIntermediateCACertThumbprint": "15E96C204DDF52BE613EFD1A7FE33EAEDAA64BD0",
"ServerManagementCertificateThumbprint": "C1281CA3D3A003FB7D09C94875954049C32EF5DF",
"ClientManagementIntermediateCACertThumbprint": "A12AC78B71A741D005BE63FAC18663376FE9033C"
}
}
The following screen shot matches the example DefaultCertificates section above. In the Windows Certificate Management Console, it is possible to locate the ClientCertificateThumbprint in Local Computer\Personal.
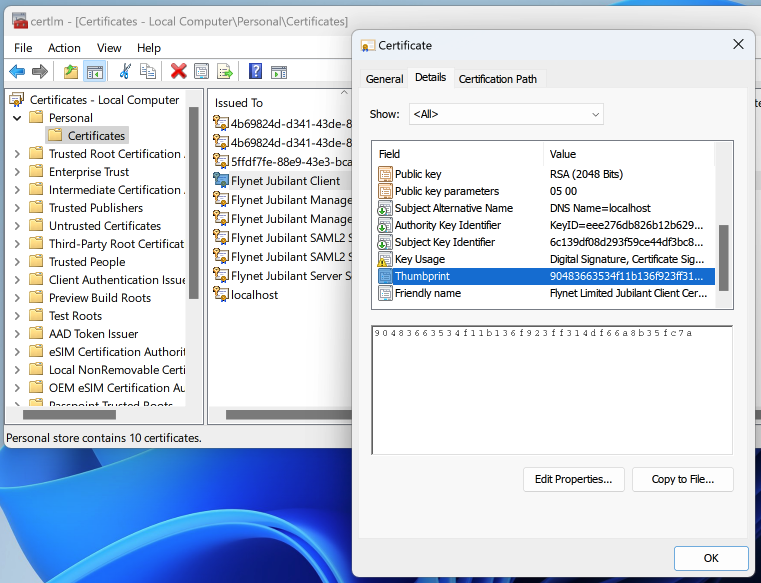
The DefaultCertificates must contain the certificate thumbnails that the process needs to configure its Connection Points.
Intermediate Certificates
If a server Connection Point is configured, the appropriate Intermediate certificate thumbnail must be provided. Jubilant requires an intermediate based on the following rules. Information on the Client and Management settings is found below.
| Client | Management | Intermediate Certificate Configuration ID Required |
|---|---|---|
| false | false | ClientIntermediateCACertThumbprint |
| false | true | ClientManagementIntermediateCACertThumbprint |
DefaultTrusts
This sets whether a server must trust the certificate of an incoming client (ServerMustTrustClient) or a client must trust the remote server's certificate (ClientMustTrustServer).
{
"DefaultTrusts": {
"ServerMustTrustClient": true,
"ClientMustTrustServer": true
}
}
ConnectionPoints
ConnectionPoint
This configuration block details where the process will find remote services (client mode) or how this process must offer services to incoming clients.
| NameKey | Mandatory | A human label to help identify what endpoint (ConnectionPoint) the entry refers to. |
| RoleId | Mandatory | A GUID identifier that Jubilant uses to identify what endpoint is being configured. |
| Client | Mandatory | A boolean value that identifies whether the Connection Point is a client or server definition. |
| Management | Mandatory | A boolean value that identifies whether the Connection Point is a Management connection or a general runtime connection. |
| ServiceUri | Mandatory | If the Connection Point is a client, then this is the hostname / port where the remote service will be found. If the Connection Point is a service, it is where the local process must listen for incoming connections. |
| ClientConfiguration | Optional | HttpClientTimeoutSeconds: The timeout in seconds before a client gives up on waiting for the service to respond. RetryMaxAttempts: The maximum number of attempts a client will try to communicate with a remote service before giving up. |
| MustTrustRemote | Optional | Overrides the DefaultTrusts.ServerMustTrustClient setting for server Connection Points or the DefaultTrusts.ClientMustTrustServer for client Connection Points. |
| CertificateThumbprint | Optional | Overrides the appropriate certificate thumbnail with the given value. |
| IntermediateCACertThumbprint | Optional | Overrides the default intermediate cert. |
Certificate Selection
Jubilant chooses the appropriate certificate based on the combination of the Client and Management boolean values given for a Connection Point. This can be overridden using the Certificate option.
| Client | Management | Intermediate Certificate Configuration ID Required |
|---|---|---|
| false | false | ServerCertificateThumbprint |
| true | false | ClientCertificateThumbprint |
| false | true | ServerManagementCertificateThumbprint |
| true | true | ClientManagementCertificateThumbprint |
Jubilant chooses the default intermediate certificate for services using these rules.
Example Client
An example client ConnectionPoint could look like the following.
{
"ConnectionPoints": [
{
"NameKey": "LoggingRuntimeClient",
"RoleId": "{30021000-0000-0000-0000-000000000000}",
"Client": true,
"Management": false,
"ServiceUri": "https://localhost:7015",
"ClientConfiguration": {
"HttpClientTimeoutSeconds": 3,
"RetryMaxAttempts": 2
},
"MustTrustRemote": false,
"Certificate": "90483663534F11B136F923FF314DF66A8B35FC7A"
}
]
}
Example Server
{
"ConnectionPoints": [
{
"NameKey": "HostScreenRuntimeService",
"RoleId": "40020000-0000-0000-0000-000000000000",
"Client": false,
"Management": false,
"ServiceUri": "https://localhost:7005"
}
]
}
Example Client and Server
{
"ConnectionPoints": [
{
"NameKey": "LoggingRuntimeClient",
"RoleId": "{30021000-0000-0000-0000-000000000000}",
"Client": true,
"Management": false,
"ServiceUri": "https://localhost:7015",
"ClientConfiguration": {
"HttpClientTimeoutSeconds": 3,
"RetryMaxAttempts": 2
}
},
{
"NameKey": "HostScreenRuntimeService",
"RoleId": "40020000-0000-0000-0000-000000000000",
"Client": false,
"Management": false,
"ServiceUri": "https://localhost:7005"
}
]
}
ClusterConnectionPoints
ClusterConnectionPoints are only applicable to the Jubilant Server process. These special Connection Points list all of the Jubilant Servers that are working as a team. This is to allow Jubilant Servers to keep server stored user settings in sync across all server machines.
ClusterConnectionPoints use the same format as normal a ConnectionPoint.
- All ClusterConnectionPoints must be of type
"Client": true. - They must provide a CertificateThumbprint.
- The remote certificate trust will fail by default. This is because the ServiceUri hostname or IP address is not in the generated certs as an allowed host. For this reason,
"MustTrustRemote": falsemust be specified.
{
"ClusterConnectionPoints": [
{
"NameKey": "ServerManagementClient",
"RoleId": "10031000-0000-0000-0000-000000000000",
"Client": true,
"Management": true,
"ServiceUri": "https://10.0.0.5:7002",
"CertificateThumbprint": "E4CDE2BBB5987CFDBA7425E3DF0B01FC46A35EEB",
"MustTrustRemote": false
},
{
"NameKey": "ServerManagementClient",
"RoleId": "10031000-0000-0000-0000-000000000000",
"Client": true,
"Management": true,
"ServiceUri": "https://10.0.0.6:7002",
"CertificateThumbprint": "E4CDE2BBB5987CFDBA7425E3DF0B01FC46A35EEB",
"MustTrustRemote": false
}
]
}